solutions
IDM SMART
A cost-efficient and quickly deployable baseline access request management solution focusing on user access lifecycle management, accelerating the approval process, and eliminating access delays.
TheFence IDM SMART offers a smooth experience for both users and approvers. It provides APIs and events to facilitate the integration of external processes and tools. It is a streamlined, NIS2-compliant Identity and Access Management solution designed for small to medium-sized businesses that need robust security without the complexity of enterprise-grade solutions.

Software as a Service
Even though it is a SaaS-based platform, it supports hybrid IT landscapes through its TheFence Agent technology. This allows businesses to manage both cloud and on-premise systems with a single solution—eliminating the need for multiple, expensive tools.
User and Role Management
The feature allows businesses to easily manage who has access to their systems and what they can do within them. This essential functionality simplifies the administration of users and their permissions, ensuring that the right people have the right level of access, all while maintaining robust security.

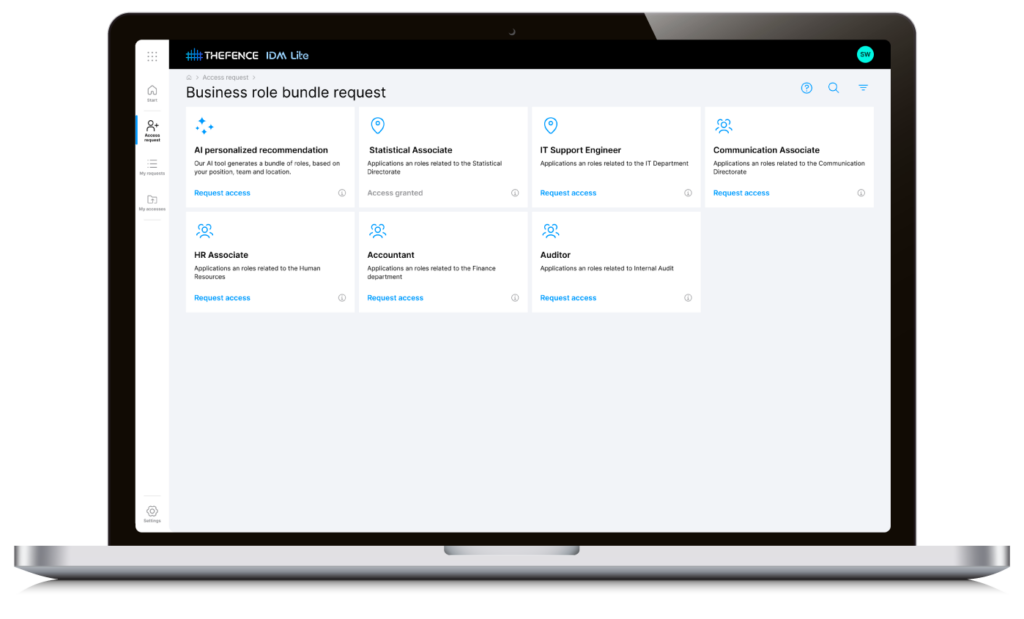
Access Request Management
It simplifies the process of requesting and granting access to systems and applications, empowering users while ensuring strict control over permissions. With a user-friendly web UI and ticketing system integrated UI (Jira Cloud), your business can efficiently handle access requests, improving security and productivity.

Access Request Approval Workflow
The Access Request Approval Workflow in IDM SMART offers the perfect balance of flexibility and simplicity, making it easy for organizations to manage access while tailoring the process to fit their unique needs.

Audit Trails & Out-Of-The Box Compliance Reports
IDM SMART not only streamlines access management but also provides robust audit trails and out-of-the-box compliance reports, ensuring your organization stays secure and audit-ready.
Efficiency
Why TheFence IDM SMART?
Simplified User Management: The API-first, lightweight cloud architecture of IDM SMART delivers cutting-edge performance, scalability, and flexibility, transforming how your organization handles access management.
Cost-Effective: Full-fledged IDM systems often come with high costs associated with complex features, infrastructure requirements, and long implementation times. IDM SMART focuses on delivering essential identity and access management features, avoiding unnecessary complexity. Businesses only pay for the functionality they need, without being overwhelmed by costly extras
Fast Setup and Integration: IDM SMART is designed for rapid deployment and smooth integration, ensuring that your organization can get up and running with minimal disruption.
Try 100% free for 14 days. Cancel Anytime
What users say
Hungarian Meteorological Service
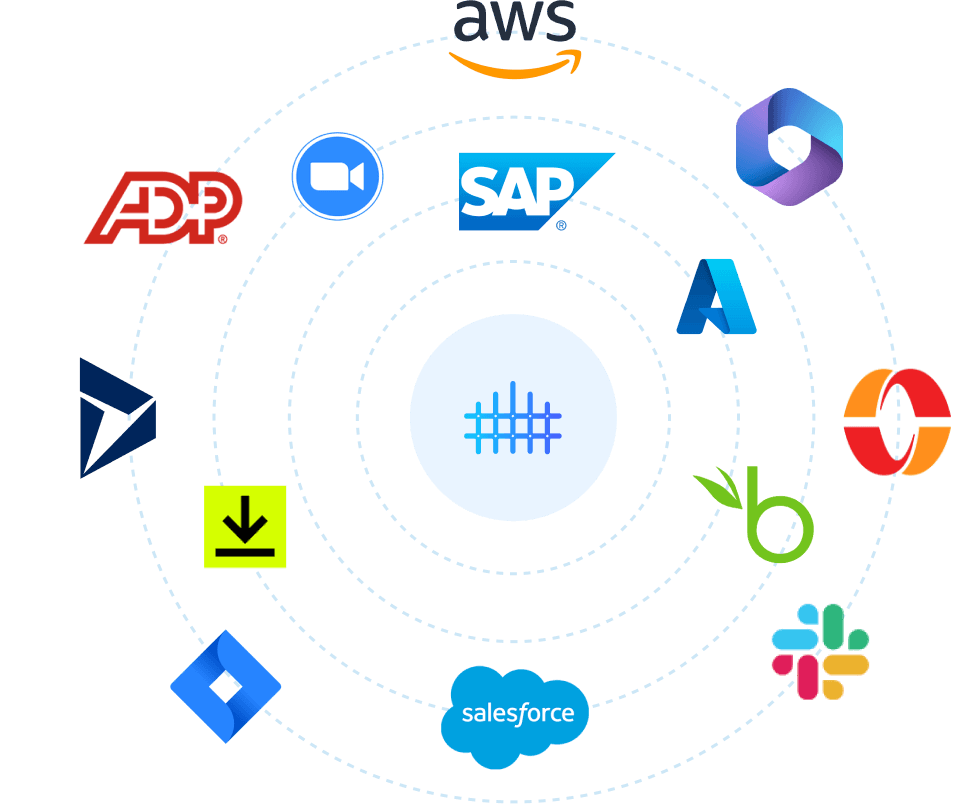
Integrate your systems to TheFence™
TheFence™ can monitor most of the most widely used solutions

Amazon Web Services
Ensure that access to resources is only granted to authorized users

Slack
Manage user access more efficiently while mitigating security risks

Salesforce
Enhance security by monitoring user access to Salesforce

Microsoft 365
Monitor and analyze the users and possible usage of service for potential security risks
Jira Software
Enhance security posture by monitoring user access

Microsoft Azure
Achieve comprehensive control over access rights

DocuSign
Detect and remove unnecessary permissions granted to users

Microsoft Entra
Achieve unified identity governance across your Microsoft ecosystem

Zoom
Identify and prevent potential security breaches through access risk monitoring

Microsoft Dynamics 365
Enhance security and minimize the risk of unauthorized access

SAP
Secure your SAP system by streamlining access risk control
Okta
Simplify identity management and strengthen access controls

Small and Medium-Sized Businesses
TheFence IDM Smart offers cost-effective, simplified user management and rapid deployment, enhancing security without extensive IT resources.

Startups and Growing Companies
IDM SMART scales with your growth, accelerates approval processes, and ensures compliance with minimal effort.

MSPs / MSSPs
This streamlined, multitenant SaaS identity management solution is tailored for MSPs and MSSPs. It provides seamless integration and swift deployment to deliver superior, scalable identity management that supports your growth and your clients' evolving needs.

Remote and Hybrid Teams
TheFence IDM SMART offers a user-friendly interface, flexible approval workflows, and enhanced security for distributed teams.









