solutions
Cross-System Segregation of Duties
At THEFENCE™ we recognize the critical importance of cross-application segregation of duties (X-SoD) in maintaining robust cybersecurity. Our SoD is designed to seamlessly integrate with your systems, ensuring that individuals are granted only the appropriate access permissions across multiple applications. We leverage automated risk analysis to identify and mitigate instances where users possess conflicting or excessive access rights. Trust us to enhance your security posture, reduce the chances of internal abuse, and keep your organization compliant.

Regular monitoring and auditing
Continuously monitor and audit the segregation of duties. This involves conducting periodic internal audits to ensure compliance with SOD policies.

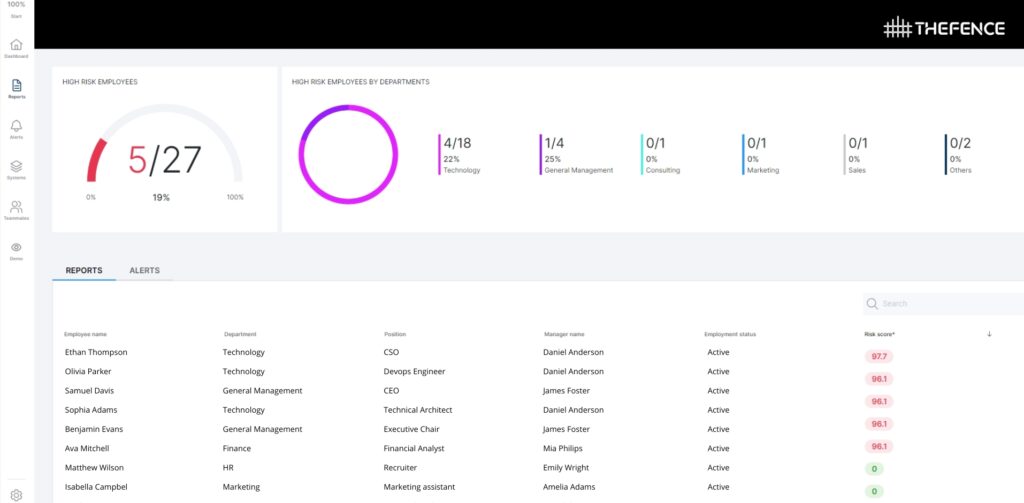
Login and MFA analytics
We collect the employees sorted by the power (access risk) they have in your IT system. Risk score calculation is based on the individuals’ access rights in the systems.
Access risk scoring
We create a risk score calculation by pattern matching, based on a collection of sensitive or conflicting access rights.

High privileges ruleset
It refers to a set of rules or permissions that grant extensive access and control over privileged resources or actions within a system or network.

Segregation of Duties ruleset
SoD policies are the processes, guidelines and/or rules that an organization has created to make sure security controls are in place while also balancing operational efficiencies and costs.
Discover your potential savings
Actionable intelligence
Automated access rights control
Unnecessary rights can be misused for fraudulent or data leakage purposes. TheFence™ automated access control solution assesses the risk of access rights to enforce the least privilege principle.
TheFence™ collects users, roles, and elementary privileges from the systems in a standardized and automated way, then it automatically performs a measurable, scoring-based risk analysis.
Try 100% free for 14 days. Cancel Anytime
In compliance with:






Cyber security awareness quiz
Integrate your systems to TheFence™
TheFence™ can monitor most of the most widely used solutions
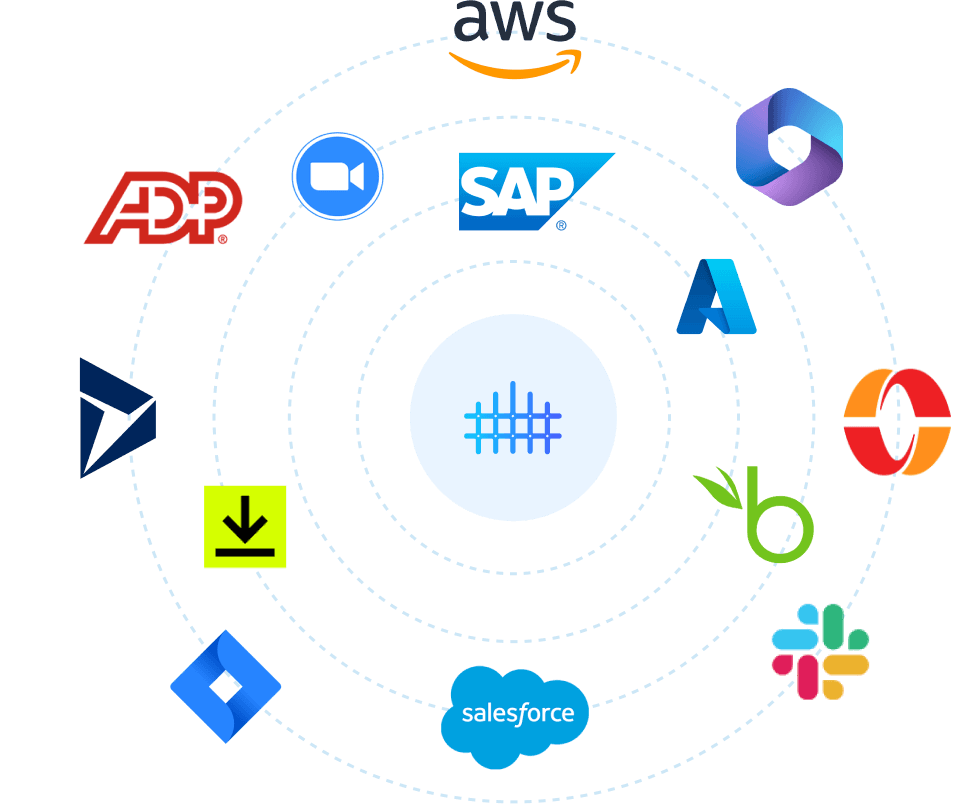

Amazon Web Services
Ensure that access to resources is only granted to authorized users

Slack
Manage user access more efficiently while mitigating security risks

Salesforce
Enhance security by monitoring user access to Salesforce

Microsoft 365
Monitor and analyze the users and possible usage of service for potential security risks
Jira Software
Enhance security posture by monitoring user access

Microsoft Azure
Achieve comprehensive control over access rights

DocuSign
Detect and remove unnecessary permissions granted to users

Zoom
Identify and prevent potential security breaches through access risk monitoring

Microsoft Dynamics 365
Enhance security and minimize the risk of unauthorized access

SAP
Secure your SAP system by streamlining access risk control

Notifications
Get up-to-date notifications to take immediate actions.

Sections & Subtasks
Get a detailed overview of your company’s security status.

Data Security
Cloud-based software for maximum security to prevent business data leakage.

Live chat support
We hold your back. Contact us for professional help.









