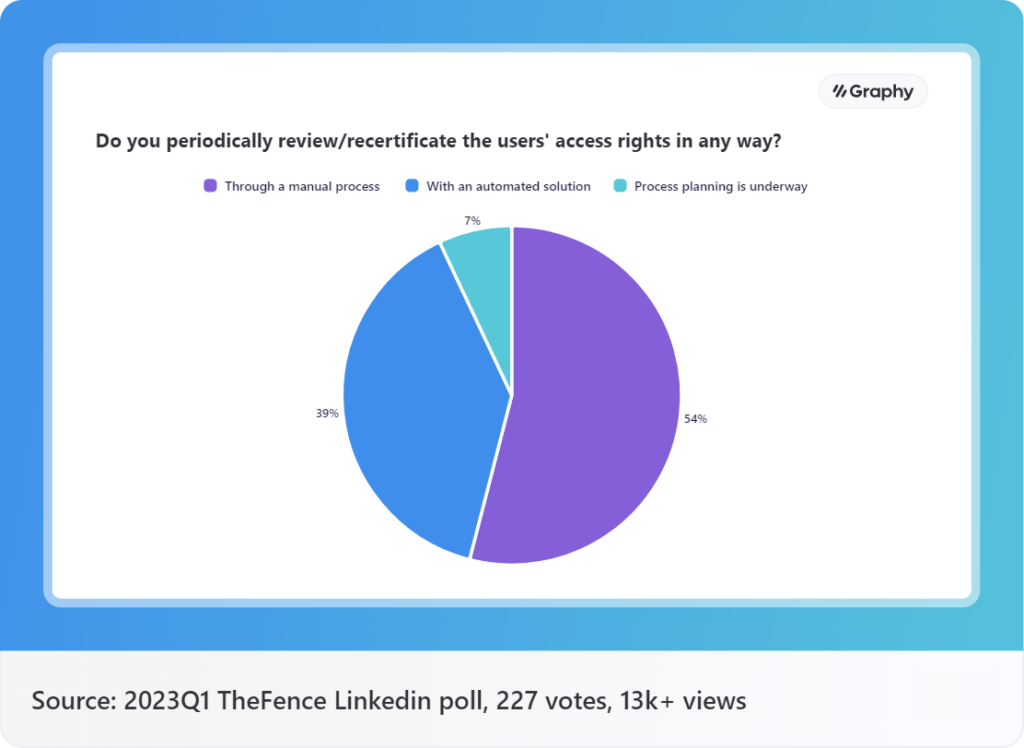
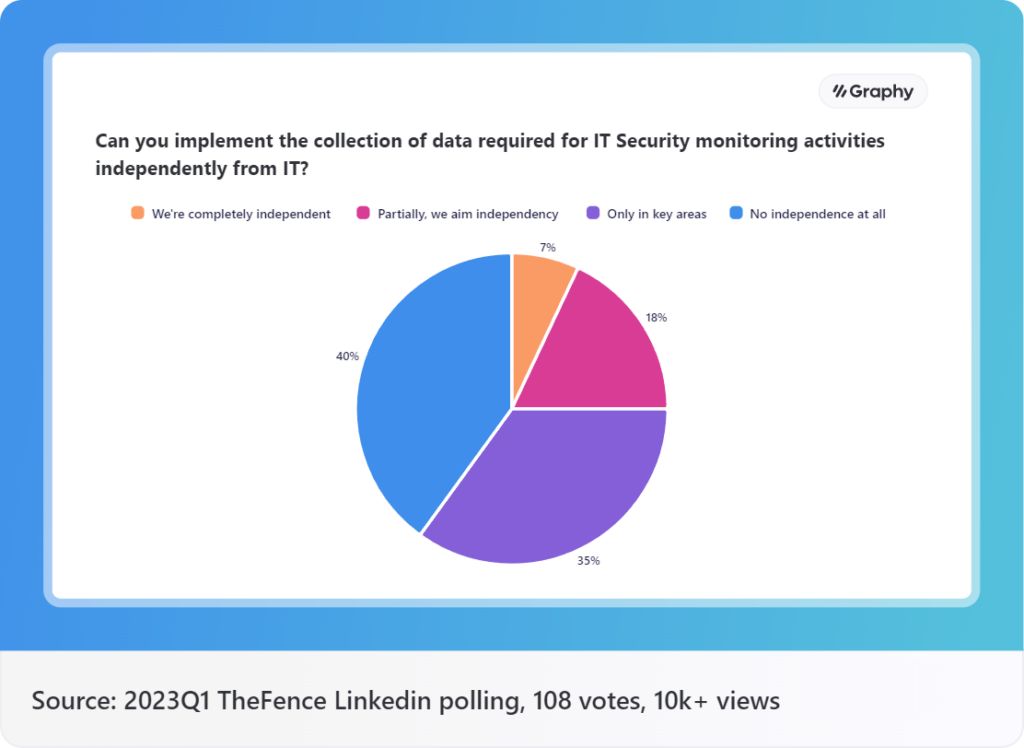
Periodic access reviews are a fundamental aspect of maintaining robust cybersecurity practices within organizations. These reviews involve the systematic evaluation and verification of user access rights to critical systems, applications, and data. By conducting these reviews at regular intervals, organizations can ensure regulatory compliance, mitigate access-related risks, and safeguard sensitive information. In this blog post, we will explore the definition, importance of compliance, and the significance of governance and accountability in periodic access reviews.
Periodic access reviews are a structured process of assessing and validating user access privileges within an organization. These reviews are conducted at regular intervals, such as quarterly, semi-annually, or annually, to ensure that access rights align with business needs and adhere to regulatory requirements. The goal is to maintain an up-to-date and accurate record of user entitlements, minimize the risk of unauthorized access, and prevent data breaches.
Compliance with industry regulations is a critical aspect of periodic access reviews. Depending on their industry, organizations must understand and adhere to relevant compliance requirements, such as GDPR, HIPAA, or PCI DSS. Periodic access reviews play a vital role in meeting these compliance obligations by ensuring that access rights are appropriate, documented, and aligned with regulatory guidelines. By incorporating compliance considerations into access reviews, organizations can demonstrate their commitment to protecting sensitive data and maintaining legal and regulatory standards.
Effective governance and accountability are essential components of successful periodic access reviews. Establishing clear ownership and responsibilities for access reviews within an organization promotes accountability and ensures a consistent and thorough review process. By defining roles and involving stakeholders from different departments, such as HR, IT, and business units, organizations can enhance the accuracy and integrity of access reviews. Governance structures also help establish guidelines, policies, and procedures for conducting reviews, ensuring consistency and adherence to best practices.
To maximize the effectiveness of periodic access reviews, cybersecurity researchers recommend the following best practices:
- Conduct Comprehensive Risk Assessments: Before initiating access reviews, perform thorough risk assessments to identify critical systems, data assets, and potential vulnerabilities. Understanding the risks associated with access rights enables organizations to prioritize efforts and allocate resources effectively.
- Involve Stakeholders: Engage various stakeholders, including business owners, system administrators, and IT teams, in the access review process. Collaboration ensures that access rights align with business needs, improves accountability, and reduces the risk of unauthorized access.
- Leverage Automation Tools: Embrace automation tools and technologies to streamline access reviews and improve efficiency. Automated solutions can help identify access anomalies, validate user entitlements, and enforce segregation of duties (SoD) policies.
- Implement Continuous Monitoring: Recognize that periodic access reviews alone may not suffice. Establish continuous monitoring practices to detect and respond to unauthorized access attempts, unusual access patterns, or changes in user privileges promptly. Continuous monitoring enhances security resilience and reduces the window of exposure to potential threats.
- Maintain Detailed Audit Logs and Reporting: Ensure comprehensive documentation of access review processes, including the individuals involved, access permissions assessed, and any modifications made. Robust audit logs and reporting capabilities facilitate regulatory audits, internal investigations, and the identification of potential access anomalies or security incidents.
Conclusion
Periodic access reviews are critical for achieving regulatory compliance and bolstering overall security posture. By focusing on the definition of access reviews, highlighting the importance of compliance, and emphasizing governance and accountability, organizations can establish a solid foundation for access control. By incorporating these best practices, organizations can strengthen their access review processes, mitigate risks, and ensure the confidentiality, integrity, and availability of critical data assets. Periodic access reviews, when conducted with proper governance and accountability, enable organizations to proactively identify and address access-related vulnerabilities, ensuring a strong defense against unauthorized access and potential data breaches.
It is crucial for organizations to extend their access review processes to encompass suppliers and implement robust vendor management practices. This includes conducting due diligence, assessing the security posture of suppliers, defining access privileges, and regularly reviewing and monitoring their access rights. By extending access reviews to suppliers, organizations can ensure that their entire supply chain is secure, mitigating the risks associated with unauthorized access and potential data breaches originating from external sources.
By understanding the definition of periodic access reviews, emphasizing compliance requirements, and prioritizing governance and accountability, organizations can enhance their approach to access reviews. Clear ownership, stakeholder involvement, and the establishment of guidelines and policies ensure that access rights are aligned with business needs and regulatory standards. Additionally, leveraging automation tools streamlines the review process, improves efficiency, and reduces the likelihood of human error.
Implementing comprehensive risk assessments enables organizations to identify critical systems and vulnerabilities, allowing them to allocate resources effectively and prioritize efforts in securing sensitive data. Continuous monitoring goes beyond periodic access reviews, providing real-time visibility into access patterns and potential threats. By maintaining detailed audit logs and reporting, organizations can demonstrate compliance, support regulatory audits, and effectively investigate any access anomalies or security incidents.