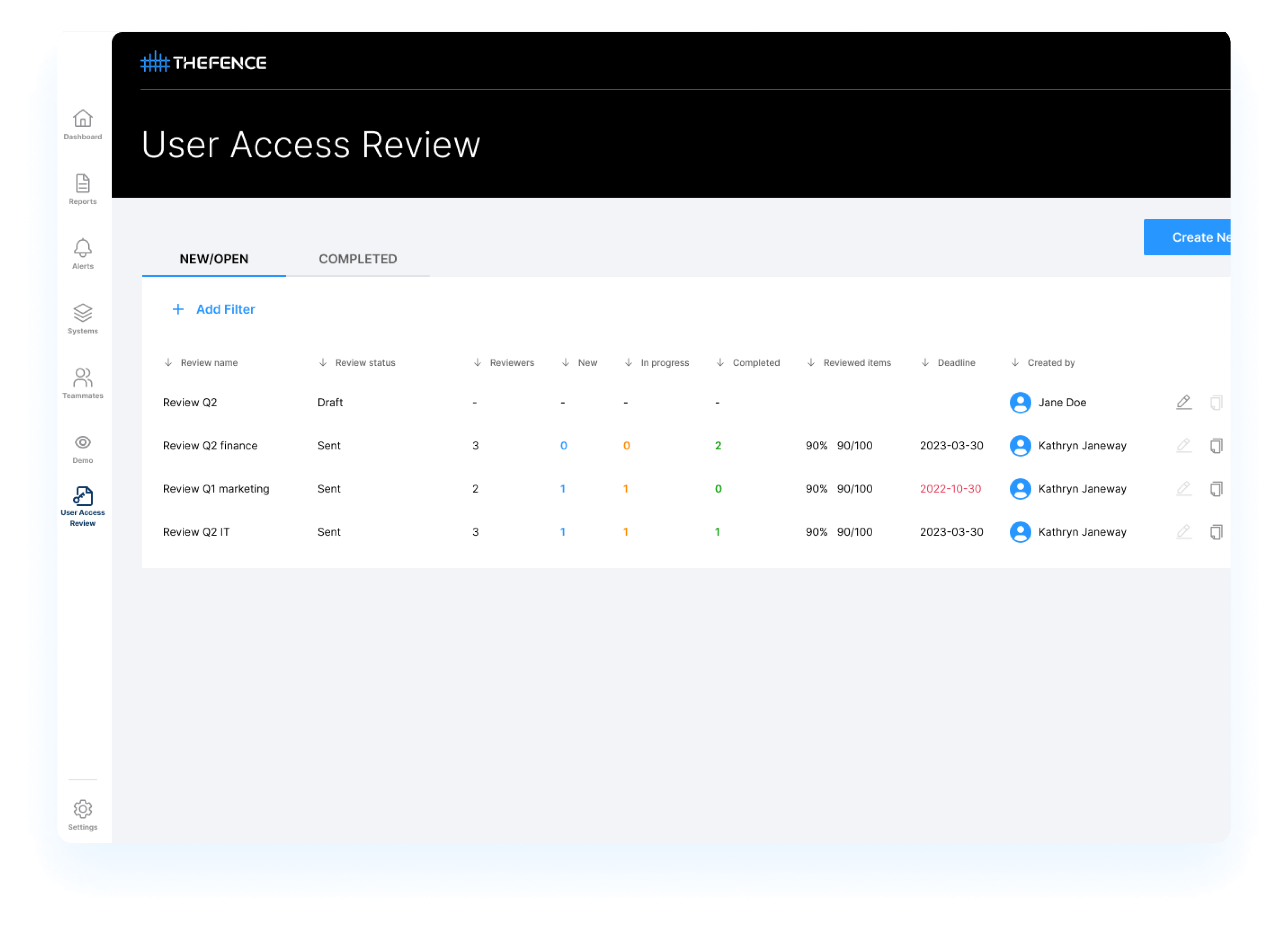
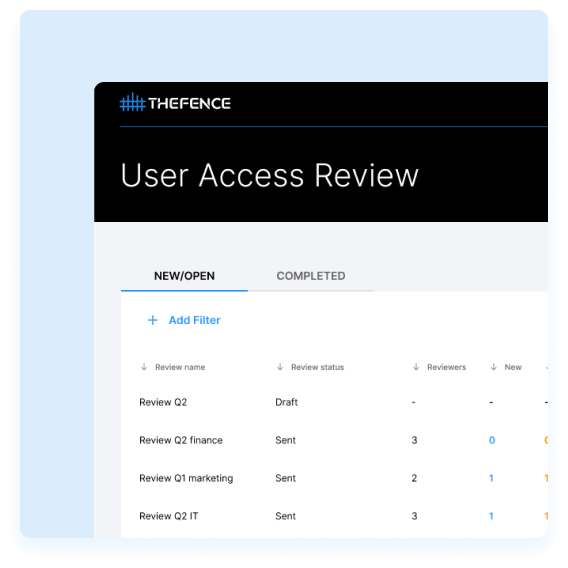
Streamline Your Access Review Process with TheFence's Automated Solution
Say Goodbye to Manual Access Reviews with TheFence's Automated Solution. The goal of user access review in the cloud is to grant appropriate access to resources and data while preventing unauthorized access

Improve security
Fortify your cloud security with automated user access reviews. Detect and eliminate unauthorized access privileges, reducing the risk of data breaches and cyber attacks.

Reduce costs
Maximize your resources and minimize costs with user access review. TheFence identifies and removes unused accounts and access privileges, helping you optimize licensing and subscriptions.

Maximize transparency
TheFence sends notifications and alerts directly to your company’s communication channels so there’s maximum awareness. Nothing blocks the flow of information.

Ensure compliance
Our solution helps you meet regulatory requirements such as HIPAA, PCI DSS, and GDPR in order to avoid penalties, legal action - or even the constant headaches, that auditors might cause.

Boost productivity
Take your productivity to the next level with access review. TheFence guarantees your employees have the resources they need to deliver outstanding results.

Power-up of AI
AI-powered tools can automate the process of access review by analyzing access logs, identifying anomalies and patterns and flagging risky access attempts.
Why automated user access review saves time and efforts for your business?

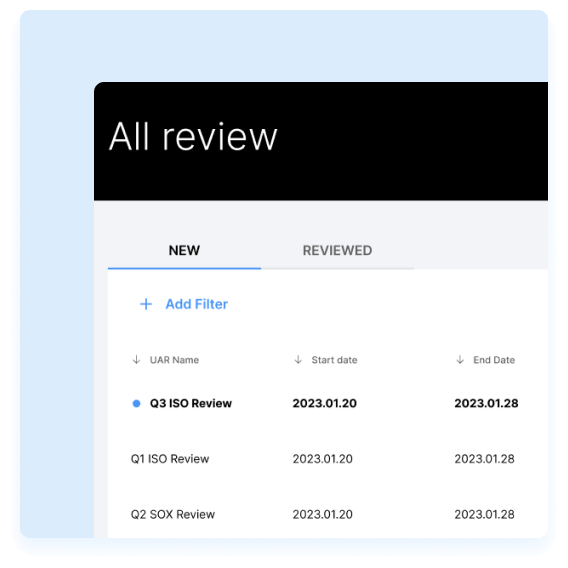
The review management and orchestration works like a charm

Decisions can be quickly turned into action

Administration, results, proofs at your fingertips

Your reviews will be full scaled, deep, accurate and super fast
What can go wrong in your manual user access reviews?
- Only the user’s employment status is reviewed, and their rights and roles are never checked.
- The review process is not documented, making it impossible to track who reviewed what and when.
- The identified problems are only corrected with significant delays or not at all.
- The examination of conflicting rights is excluded from the review process.
- The review process is not consistent and not regulated internally.
- Only the users of the employees are reviewed.
- No one checks the rights of technical users.
- The external users are also excluded from the review.
- The collected data are not documented, and the scope differs system by system.
- The rights of the users are checked against external, manually simplified lists.
- The contents of the roles are not collected and reviewed.
- The review is not conducted by the business owner / data owner but by the IT administrators, so no one will notice and follow business changes in the access profile contents.
- The reviewer passes the task on to someone else (with or without the sufficient knowledge).
- The expertise of the reviewers ranges widely, and some do not have adequate knowledge for the review.
- The reviewer is not aware of the business risks and conflicts related to the access rights.
- The reviewer must also check their own entitlements, which is inherently conflicting.
- They manually manage, coordinate and monitor the review process.
- The review is complex, incomplete, and difficult to enforce through the whole organization.
- The process takes a long time, and it is difficult to get responses from the reviewers.
- The IAM tool (if any) does not (or cannot) be configured for user access review process
What users say
Why us?
- More than 100.000 users being monitored
- Innovative next-generation software technology
- Unique scoring based risk analysis with more than 10.000 rule sets
Automate your access review with TheFence™
Experience a new level of efficiency, security, and compliance with TheFence's advanced access review solution
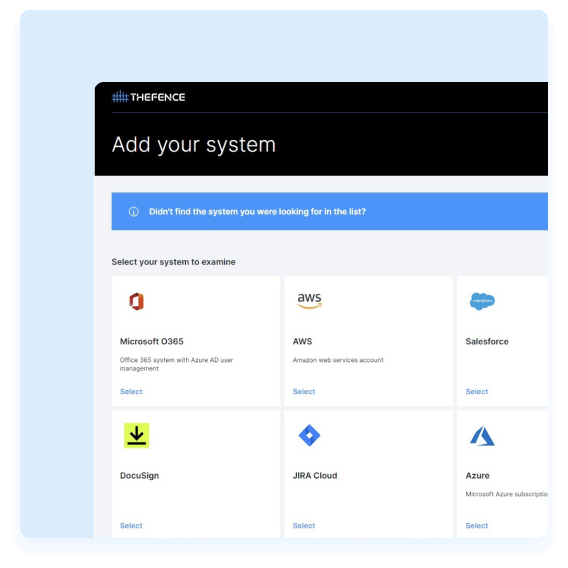
Built in cloud integrations
Manage access rights from integrated systems and ensure compliance with industry standards and regulations such as the least privilege principle and segregation of duties.




Automated user identification
TheFence™ can seamlessly connect to HR systems, extract data and identify users automatically.
Access entitlement analysis and risk scoring
We help reviewers make better decisions by showing access risk scores.


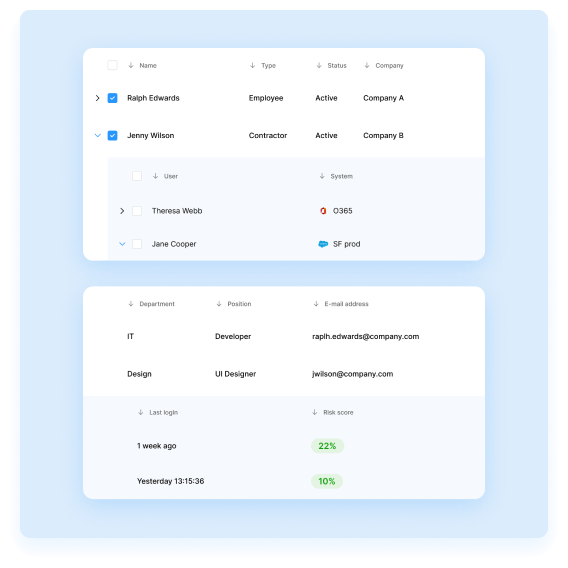


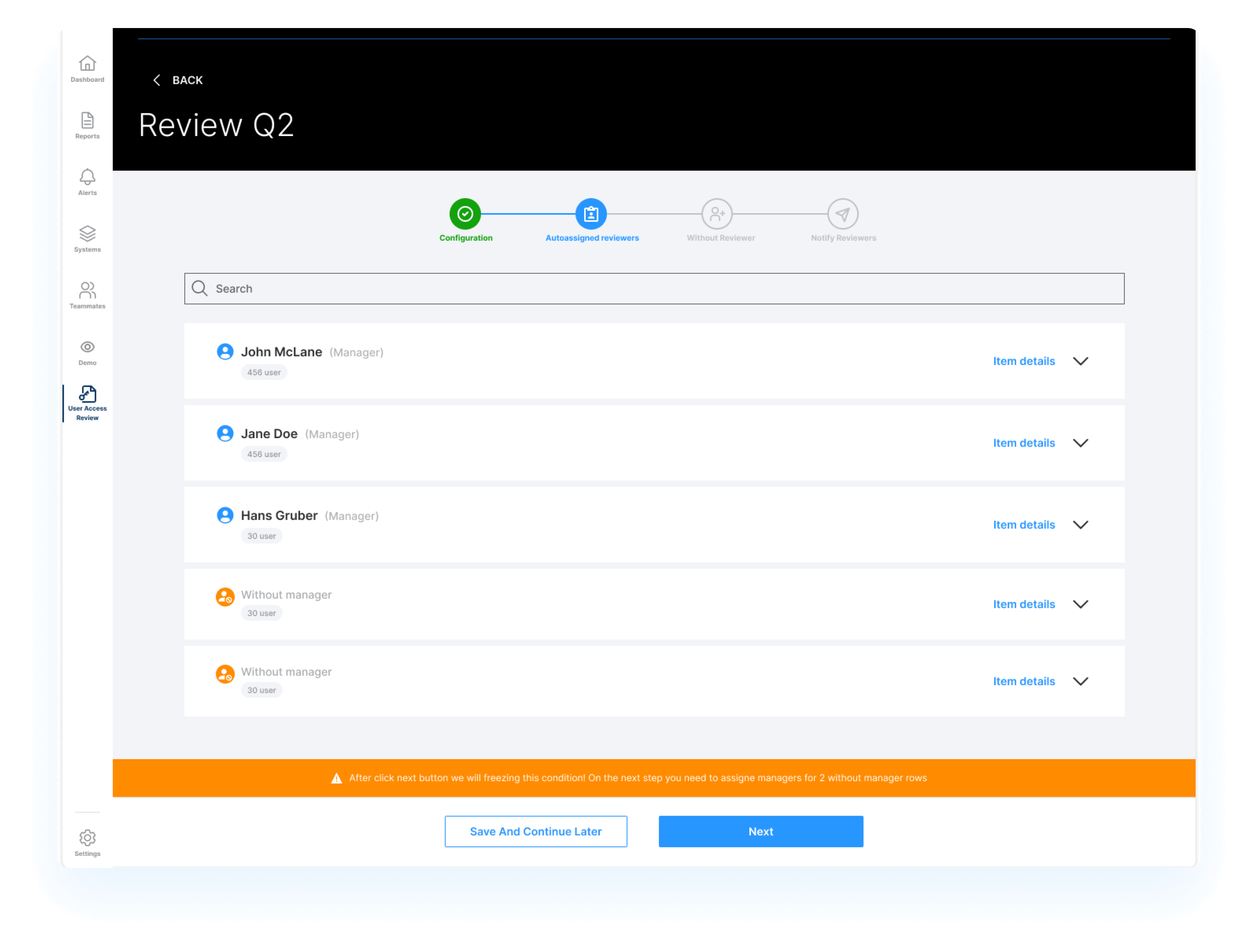
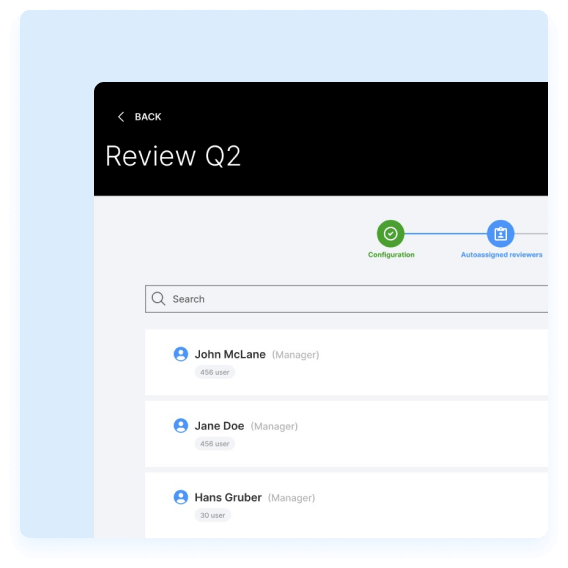
Automated reviewer assignment and task generation
You can streamline the process by assigning reviewers automatically and generating tasks for them.
Outlier detection,
auto- recommendation
We enable reviewers to enhance their decision-making capabilities by proposing decisions using AI.


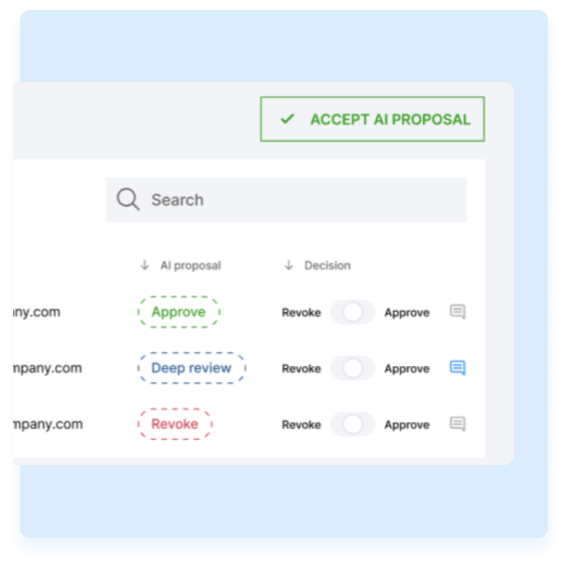
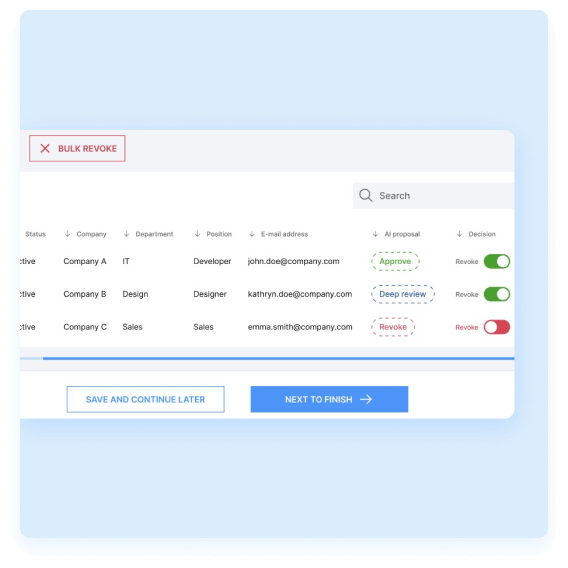


Guided user interface and decision support for reviewers
TheFence™ provides a user-friendly interface that offers reviewers AI-powered recommendations, aiming to enhance the accuracy and efficiency of decision-making during the review process.
Access review cockpit for CISO or power users
TheFence™ solution provides a centralized and comprehensive interface where they can efficiently review and manage access permissions and privileges


Keep everyone satisfied
Efficiency, accuracy, consistency, scalability and compliance: all key stakeholders
benefit from the advantages of automation
Oswald (CEO)
"We are constantly criticized by auditors for leaving the user access reviews unfinished, incomplete. Furthermore, we make poor decisions, this control simply does not work."

Bob (CISO)
"We spend endless hours of coordinating the managers on the User Access Review."

Jason (Data owner)
"I am being asked to make decisions about user access without any assistance regarding what entitlements I should revoke."

Our accomplishments



What users say
Why us?
- Actionable intelligence and automation platform
- Easy-to-use, easy-to-deploy
- Available both on-prem and in the cloud
Integrate your systems to TheFence™
TheFence™ can monitor most of the most widely used solutions
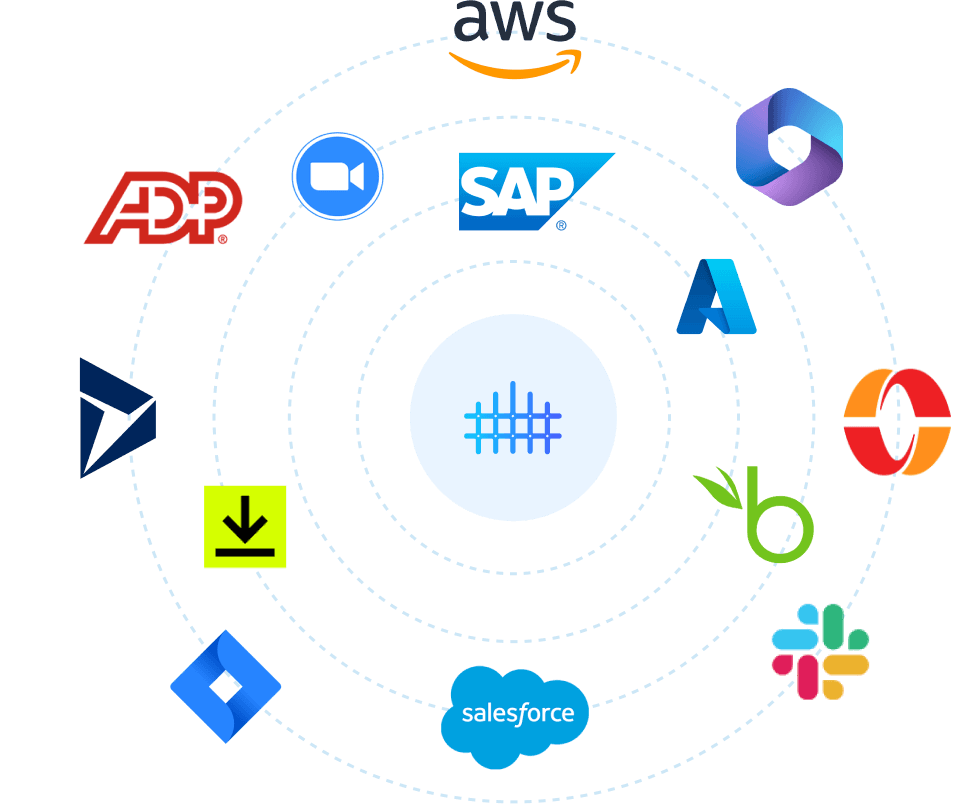

Amazon Web Services
Ensure that access to resources is only granted to authorized users

Slack
Manage user access more efficiently while mitigating security risks

Salesforce
Enhance security by monitoring user access to Salesforce

Microsoft 365
Monitor and analyze the users and possible usage of service for potential security risks
Jira Software
Enhance security posture by monitoring user access

Microsoft Azure
Achieve comprehensive control over access rights

DocuSign
Detect and remove unnecessary permissions granted to users

Microsoft Entra
Achieve unified identity governance across your Microsoft ecosystem

Zoom
Identify and prevent potential security breaches through access risk monitoring

Microsoft Dynamics 365
Enhance security and minimize the risk of unauthorized access

SAP
Secure your SAP system by streamlining access risk control
Okta
Simplify identity management and strengthen access controls
Any questions?
Check out the FAQs
Still have unanswered questions and need to get in touch?
User access review refers to the process of evaluating and verifying the users and their access rights within an organization’s IT environment. This review ensures that employees or other authorized individuals have appropriate access to the resources they need to perform their job functions, while also preventing unauthorized access to sensitive data or systems.
During a user access review, administrators or data owners (mostly business line managers) examine the access rights assigned to each user account, checking to ensure that each account is only granted the minimum level of access necessary to perform its intended purpose. Any discrepancies or unauthorized access should be identified and corrected, which helps to maintain the security and integrity of the organization’s data and systems.
User access reviews are typically conducted on a periodic basis, such as annually or semi-annually, as part of an organization’s overall information security management program.
- Protecting Sensitive Data: User access reviews ensure that only authorized individuals have access to sensitive data and systems within the organization. By reviewing user access rights regularly, businesses can prevent unauthorized access, data breaches, and other security incidents that could result in significant financial and reputational harm.
- Compliance with Regulations: Many industries are subject to regulatory requirements that mandate regular user access reviews. For example, the healthcare industry is required to comply with HIPAA regulations that require regular audits of user access to electronic protected health information (ePHI). Conducting user access reviews helps businesses ensure compliance with these regulations.
- Identifying Security Threats: User access reviews can help businesses identify potential security threats, such as users with excessive or conflicting access rights.
- Enhancing Operational Efficiency: Conducting regular user access reviews can help businesses ensure that access rights are appropriate for each user’s job function. This can help to reduce the potential for errors or inefficiencies that could impact productivity and business operations.
- Protecting the Reputation of the Business: Businesses that experience data breaches or other security incidents can suffer significant reputational harm. Conducting regular user access reviews can help to prevent security incidents and protect the reputation of the business.
- Unauthorized Access: When users are granted access to systems or data they should not have access to, this can lead to data breaches, intellectual property theft, or other unauthorized activity.
- Excessive Access: Users who have access to more data or systems than they need to perform their job functions pose a risk to themselves and to the organization. This can result in data breaches, insider threats, or other security incidents. If their user credentials were stolen (e.g. phishing attack), the excessive access rights can be be very useful for the attacker.
- Inactive Accounts: When user accounts are left active even after the user has left the organization or no longer requires access, this can pose a risk to the organization. Inactive accounts can be exploited by attackers, who can use them to gain unauthorized access to the organization’s systems and data. In this case they can be hard to detect and identify as the previous owner will be in the activity logs.
- Shared Accounts: When multiple users share a single account, this can make it difficult to track who is accessing data and systems. This can pose a risk to the organization, as it can be difficult to determine who is responsible for any unauthorized activity that occurs.
- Weak Passwords: Users who have weak passwords or use the same password for multiple accounts pose a risk to the organization. This can make it easier for attackers to gain access to the organization’s systems and data.
The frequency of conducting user access reviews can vary depending on the size and complexity of the organization, as well as regulatory requirements. However, we believe that asset owners should conduct regular and periodic user access reviews. Some organizations may need to conduct reviews more frequently, such as every six months or quarterly, to ensure compliance with regulations or to address specific security risks.
It is important to note that user access reviews should also be conducted whenever there is a significant change in the organization, such as a merger or acquisition, a change in business operations, or a new system implementation. Additionally, if a security incident or breach occurs, a user access review should be conducted immediately to identify any vulnerabilities and address them promptly.
The user access review process is incomplete:
- Only the user’s employment status is reviewed, and their rights and roles are never checked.
- The review process is not documented, making it impossible to track who reviewed what and when.
- The identified problems are only corrected with significant delays or not at all.
- The examination of conflicting rights is excluded from the review process.
- The review process is not consistent and not regulated internally.
The scope of the examined data is incomplete:
- Only the users of the employees are reviewed.
- No one checks the rights of technical users.
- The external users are also excluded from the review.
- The collected data are not documented, and the scope differs system by system.
- The rights of the users are checked against external, manually simplified lists.
- The contents of the roles are not collected and reviewed.
The examination is not performed by the appropriate person:
- The review is not conducted by the business owner / data owner but by the IT administrators, so no one will notice and follow business changes in the access profile contents.
- The reviewer passes the task on to someone else (with or without the sufficient knowledge).
- The expertise of the reviewers ranges widely, and some do not have adequate knowledge for the review.
- The reviewer is not aware of the business risks and conflicts related to the access rights.
- The reviewer must also check their own entitlements, which is inherently conflicting.
They use the wrong tools, or they don’t have tools for user access review:
- They manually manage, coordinate and monitor the review process.
- The review is complex, incomplete, and difficult to enforce through the whole organization.
- The process takes a long time, and it is difficult to get responses from the reviewers.
- The IAM tool (if any) does not (or cannot) be configured for user access review process.
















