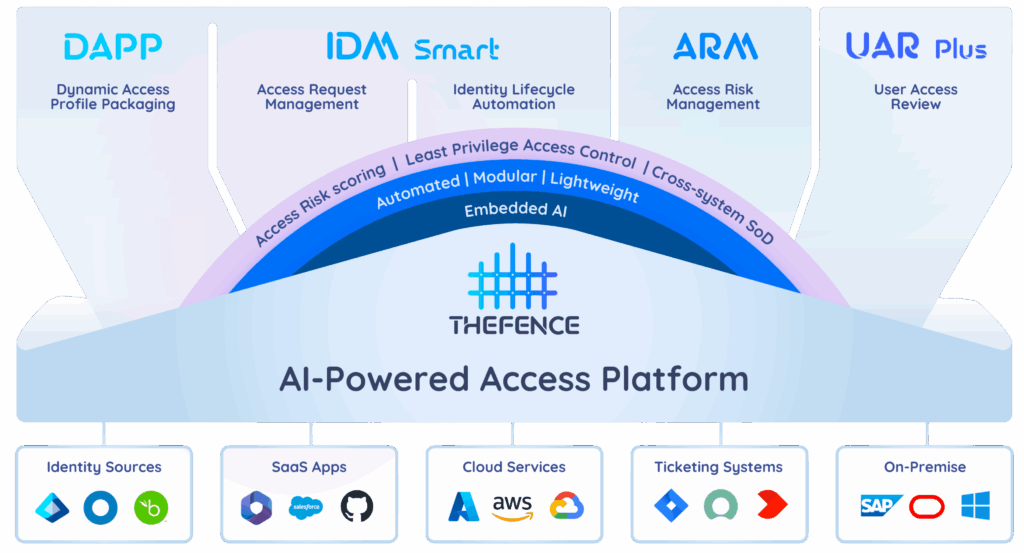
TheFence™ AI-Powered Access Platform
THEFENCE™ is an automated, modularly built, AI-powered, lightweight identity governance and administration (IGA) platform tailored for organizations of all sizes.
Defend Your Digital Assets with TheFence™
Our mission is to ensure that the right people have the right level of access to the right resources at the right time.
AI-powered access rights control
TheFence™ assesses the risk associated with access rights, ensuring the Principle of Least Privilege (PoLP). By systematically and automatically gathering user data, roles, and elementary privileges, TheFence™ conducts a measurable, scoring-based risk analysis to fortify your security measures.
We harness the capabilities of machine learning and generative AI across various facets of our systems, including but not limited to risk scoring, anomaly detection, and risk explanation.
Try 100% free for 14 days. Cancel Anytime
In compliance with:






Top 5 TheFence™ innovations
The first AI co-pilot in user access review and AI
powered access profiling solution in the industry: an innovative, cloud-based software-as-a-service (SaaS) solution that automates the periodic review of the users’ (employees, suppliers, technical users) access rights in a company’s digital environment.
Easy-to-deploy, resource-friendly, modular solution stack.
Discovery of access risks down to the deepest possible
level of elementary entitlement objects.
Ability to detect cross-application conflicts of interest.
A scoring-based, AI-supported metric system quantifying the users’ entitlement risks.
What users say
Hungarian Meteorological Service
Cyber Security Awareness Quiz
Integrate your systems to TheFence™
TheFence™ can monitor most of the most widely used solutions

Amazon Web Services
Ensure that access to resources is only granted to authorized users

Slack
Manage user access more efficiently while mitigating security risks

Salesforce
Enhance security by monitoring user access to Salesforce

Microsoft 365
Monitor and analyze the users and possible usage of service for potential security risks
Jira Software
Enhance security posture by monitoring user access

Microsoft Azure
Achieve comprehensive control over access rights

DocuSign
Detect and remove unnecessary permissions granted to users

Microsoft Entra
Achieve unified identity governance across your Microsoft ecosystem

Zoom
Identify and prevent potential security breaches through access risk monitoring

Microsoft Dynamics 365
Enhance security and minimize the risk of unauthorized access

SAP
Secure your SAP system by streamlining access risk control
Okta
Simplify identity management and strengthen access controls

UAR challenges
Our clients were facing challenges in managing the periodic User Access Review (UAR) process. The preparation phase is time-consuming and requires major HR efforts and tedious manual processes. The review process is complex, extensive and difficult to administer. We assisted them in automating the preparation, orchestration, and documentation of the UAR process steps. We also incorporated an AI platform in the product to support the data owners’ decisions.

Risk proportionality
Some of our customers were struggling to measure and demonstrate access risks to auditors and senior management. TheFence enabled them to quantify risks with its innovative risk scoring and generate reports and alerts automatically. As a result, those customers are aware of the riskiest identities (employees, third-party persons) with excessive or conflicting access rights.
Substitution of IAM project
A customer was under compliance pressure related to identity requirements due to a lack of an IAM solution integrated with their ticketing system. THEFENCE™ provided them with an identity & access inventory for their riskiest systems and implemented an access risk monitoring process. As a result, the ticketing system was supplemented with THEFENCE access risk control platform, and finally passed the audit successfully.

Insider incident prevention
Many clients realized that numerous incidents were related to unnecessary or conflicting access rights. Our preventive solution enabled them to react by closely monitoring access risks at the individual level. We identified the identities possessing the most critical administrative and business functions of very high threats within their access profiles. By removing these, they have significantly reduced their attack profile.
Why
TheFence™?
Who is TheFence™ for?
TheFence™ is designed to enable comprehensive access risk management, streamline compliance, and enhance security posture with automated risk analysis and tailored reporting capabilities.
CISO / IT Security Team
Achieve a balanced and effective security posture by leveraging TheFence's advanced risk analysis capabilities to measure and score access risks, ensuring comprehensive protection and control within your organization.

Compliance and Governance Officers
Streamline access control, gain visibility, and mitigate unauthorized access risks effortlessly with our automated risk assessments, intuitive interface, and robust reporting capabilities, ensuring efficient and effective compliance management.

Executive Management
Stay audit-ready and make data-driven decisions with our automated solution, offering standardized collection of users, roles, and access objects, advanced risk analysis capabilities, and AI-powered recommendations to manage access risks effectively.

System Administrators and IT Operation Teams
Achieve complete visibility and control over access privileges, streamline user provisioning and deprovisioning, maintain compliance, and minimize the risk of unauthorized access.

MSPs / MSSPs
Elevate your access management capabilities with THEFENCE™, delivering tailored actionable reports to key departments like IT security, internal audit, CFO, CRO, or HR, ensuring timely insights for stakeholders to take prompt risk mitigation actions.

About us
The manufacturer of THEFENCE™ is XS Matrix, an IT security company, headquartered in Miami, FL, USA, and Budapest, Hungary, and having further operations in Frankfurt, Germany as well as Kuala Lumpur, Malaysia.
The founders of XS Matrix are IT security professionals. One of them started as an IT auditor, and then spent 10+ years as a CISO in the financial sector (international banks), where he specialized in preventing and detecting internal fraud and data leakage. Despite encountering challenges and weak solutions in access rights control over the years, his extensive, hands-on experience helped him create his method for risk-based access profile reviews, which was the basis for the development of THEFENCE, an automated access rights control software and SaaS solution.

Any questions?
Check out the FAQs
Still have unanswered questions and need to get in touch?
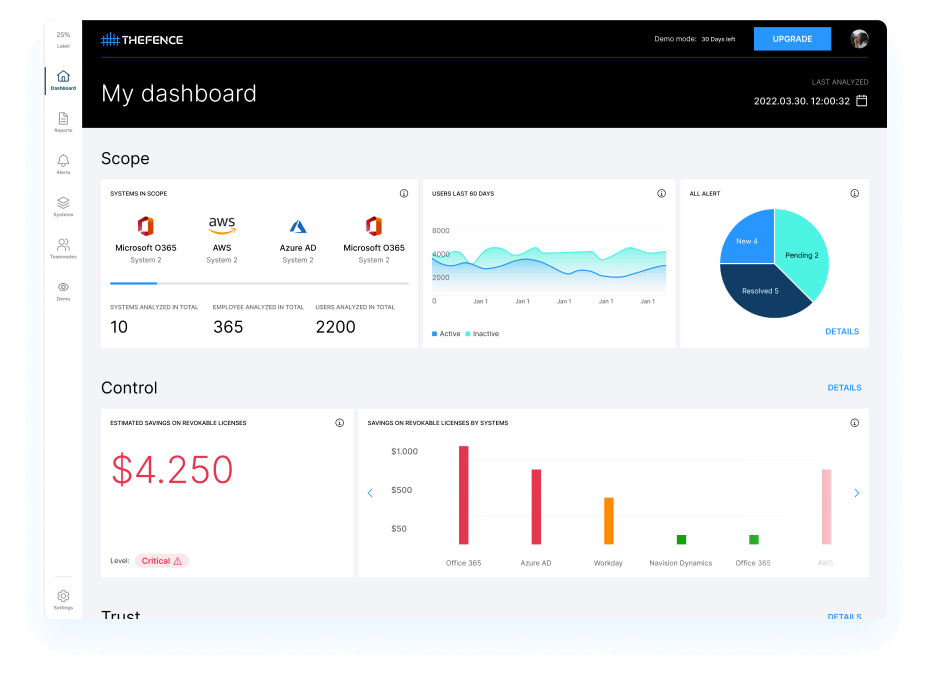
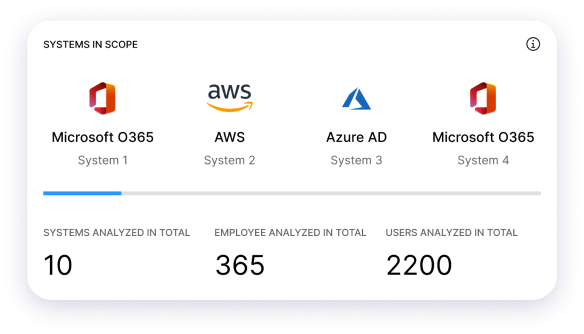
Excessive access rights underestimated security problems, many times being the root cause of incidents, thus everyone needs to be aware of how risky rights your employees have. Access control problems may also affect your license cost: you can reach cost savings on them by automating control.
TheFence can be connected to your other cloud applications. We show you in our easy-to-follow video how to set up the connection.
Your applications are mostly in the cloud, so the best way to ensure their access control by a cloud solution as well.
User access review refers to the process of evaluating and verifying the users and their access rights within an organization’s IT environment. This review ensures that employees or other authorized individuals have appropriate access to the resources they need to perform their job functions, while also preventing unauthorized access to sensitive data or systems.
During a user access review, administrators or data owners (mostly business line managers) examine the access rights assigned to each user account, checking to ensure that each account is only granted the minimum level of access necessary to perform its intended purpose. Any discrepancies or unauthorized access should be identified and corrected, which helps to maintain the security and integrity of the organization’s data and systems.
User access reviews are typically conducted on a periodic basis, such as annually or semi-annually, as part of an organization’s overall information security management program.
- Protecting Sensitive Data: User access reviews ensure that only authorized individuals have access to sensitive data and systems within the organization. By reviewing user access rights regularly, businesses can prevent unauthorized access, data breaches, and other security incidents that could result in significant financial and reputational harm.
- Compliance with Regulations: Many industries are subject to regulatory requirements that mandate regular user access reviews. For example, the healthcare industry is required to comply with HIPAA regulations that require regular audits of user access to electronic protected health information (ePHI). Conducting user access reviews helps businesses ensure compliance with these regulations.
- Identifying Security Threats: User access reviews can help businesses identify potential security threats, such as users with excessive or conflicting access rights.
- Enhancing Operational Efficiency: Conducting regular user access reviews can help businesses ensure that access rights are appropriate for each user’s job function. This can help to reduce the potential for errors or inefficiencies that could impact productivity and business operations.
- Protecting the Reputation of the Business: Businesses that experience data breaches or other security incidents can suffer significant reputational harm. Conducting regular user access reviews can help to prevent security incidents and protect the reputation of the business.
Any questions?
Check out the FAQs
Still have unanswered questions and need to get in touch?
Excessive access rights underestimated security problems, many times being the root cause of incidents, thus everyone needs to be aware of how risky rights your employees have. Access control problems may also affect your license cost: you can reach cost savings on them by automating control.
TheFence can be connected to your other cloud applications. We show you in our easy-to-follow video how to set up the connection.
Your applications are mostly in the cloud, so the best way to ensure their access control by a cloud solution as well.
User access review refers to the process of evaluating and verifying the users and their access rights within an organization’s IT environment. This review ensures that employees or other authorized individuals have appropriate access to the resources they need to perform their job functions, while also preventing unauthorized access to sensitive data or systems.
During a user access review, administrators or data owners (mostly business line managers) examine the access rights assigned to each user account, checking to ensure that each account is only granted the minimum level of access necessary to perform its intended purpose. Any discrepancies or unauthorized access should be identified and corrected, which helps to maintain the security and integrity of the organization’s data and systems.
User access reviews are typically conducted on a periodic basis, such as annually or semi-annually, as part of an organization’s overall information security management program.
- Protecting Sensitive Data: User access reviews ensure that only authorized individuals have access to sensitive data and systems within the organization. By reviewing user access rights regularly, businesses can prevent unauthorized access, data breaches, and other security incidents that could result in significant financial and reputational harm.
- Compliance with Regulations: Many industries are subject to regulatory requirements that mandate regular user access reviews. For example, the healthcare industry is required to comply with HIPAA regulations that require regular audits of user access to electronic protected health information (ePHI). Conducting user access reviews helps businesses ensure compliance with these regulations.
- Identifying Security Threats: User access reviews can help businesses identify potential security threats, such as users with excessive or conflicting access rights.
- Enhancing Operational Efficiency: Conducting regular user access reviews can help businesses ensure that access rights are appropriate for each user’s job function. This can help to reduce the potential for errors or inefficiencies that could impact productivity and business operations.
- Protecting the Reputation of the Business: Businesses that experience data breaches or other security incidents can suffer significant reputational harm. Conducting regular user access reviews can help to prevent security incidents and protect the reputation of the business.











